Source: csrc.NIST.gov
Why NIST CSF 2.0 is the New Standard for Managing Vendor Cybersecurity Risks
In today’s world, no piece of technology is an island. Whether you are using a laptop, a smartphone, or a cloud service, that product was built using an extensive, global network of parts, software, and people. This network is known as the Supply Chain Ecosystem.
While this interconnectedness makes technology powerful, it also introduces risk. If a single supplier has a security flaw, it can affect every organization that uses their products. This is why Cybersecurity Supply Chain Risk Management (C-SCRM) has become essential for modern business.
What Exactly is C-SCRM?
C-SCRM is a systematic process for managing your exposure to security risks throughout the entire life of a product—from the moment it is designed to the day it is retired. It helps organizations identify, assess, and mitigate risks at every level of the business.
Without these checks, organizations are vulnerable to several "hidden" threats, including:
Malicious Functionality: Hidden "backdoors" that allow hackers into your systems.
Counterfeit Devices: Fake hardware that may be unreliable or insecure.
Poor Manufacturing: Vulnerabilities created by sloppy development or manufacturing practices.
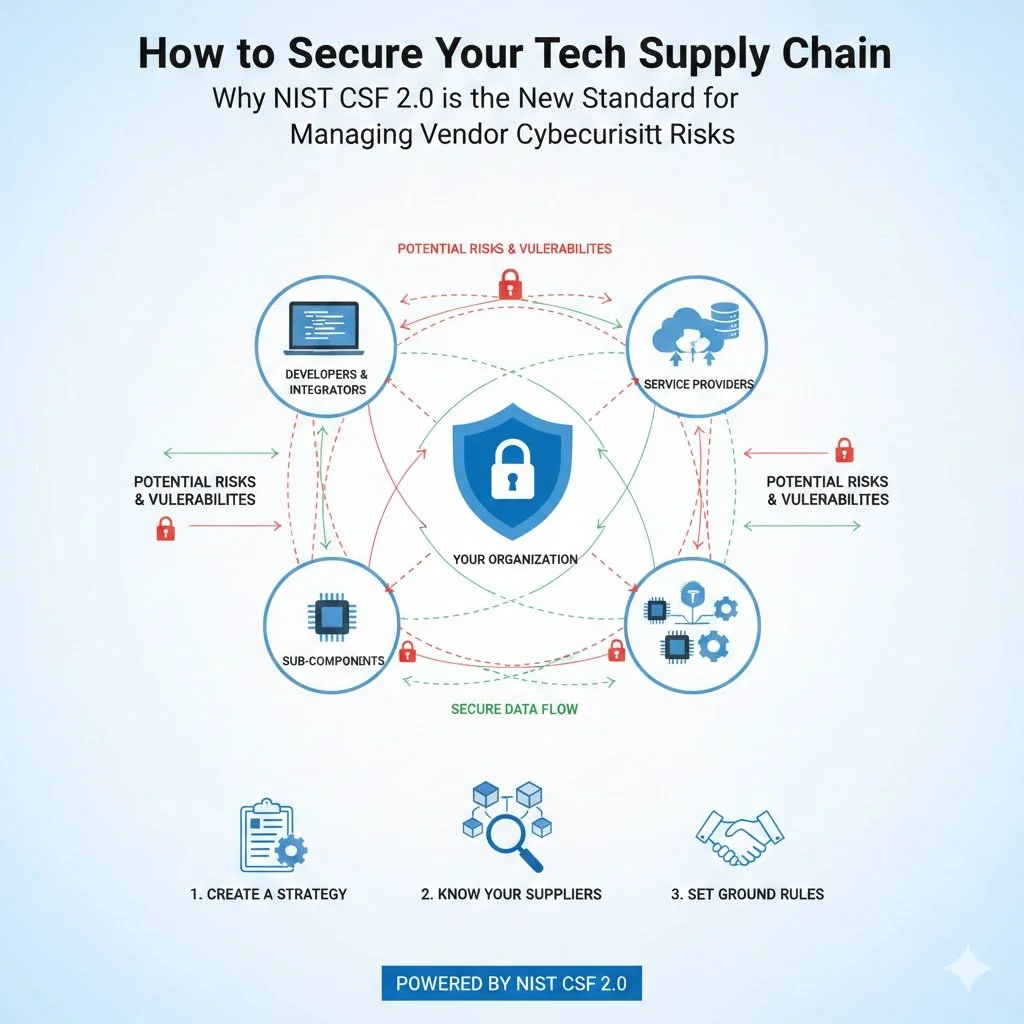
The Supply Chain Ecosystem: More Than Just Parts
The supply chain is much broader than just a factory assembly line12. It includes a variety of public and private entities:
Developers and Integrators: The people who write the code and design the systems.
Service Providers: External companies that provide data or digital services.
Sub-components: Every individual piece inside a device, such as a graphics processor or memory chip, often sourced from different countries.
How to Build a C-SCRM Capability
To manage these risks effectively, the NIST Cybersecurity Framework (CSF) 2.0 provides a roadmap for becoming a "smart acquirer" of technology. Here are the three initial activities to get started:
Create a Strategy: Establish clear objectives, policies, and processes for how your organization will handle technology risks.
Know Your Suppliers: Identify all of your technology suppliers and determine how "critical" each one is to your business. For example, a supplier with access to your sensitive data is more critical than one providing basic hardware.
Set Ground Rules: Clearly communicate security requirements to your partners. This often involves putting specific security rules into contracts, such as requiring suppliers to disclose any vulnerabilities they find.
The Bottom Line
Cybersecurity is no longer just about your own "front door". It is about ensuring that every partner and every component your business relies on is just as secure as you are. By adopting C-SCRM practices, you build a resilient business that is prepared for the complexities of the modern tech landscape.
👉 Request your customized cyber vulnerability report today and stay ahead of threats.
👉 Gain insights into your unique cybersecurity vulnerabilities with a custom report.
👉 Train your team to be your first line of defense
📞 Schedule a call today or 📧 contact us for a consultation.