Source: csrc.nist.gov
A Guide to Identifying High-Risk Vendors Using NIST CSF 2.0 Activity 2
Now that you have established a strategy for Cybersecurity Supply Chain Risk Management (C-SCRM), the next logical step is to identify exactly who is in your "supply chain ecosystem". As the recent NIST SP 1305 guide points with, you cannot treat every vendor the same way. A cloud provider holding your company’s intellectual property requires much stricter oversight than a vendor providing office furniture.
This process is known as Activity 2: Identifying and Prioritizing Suppliers.
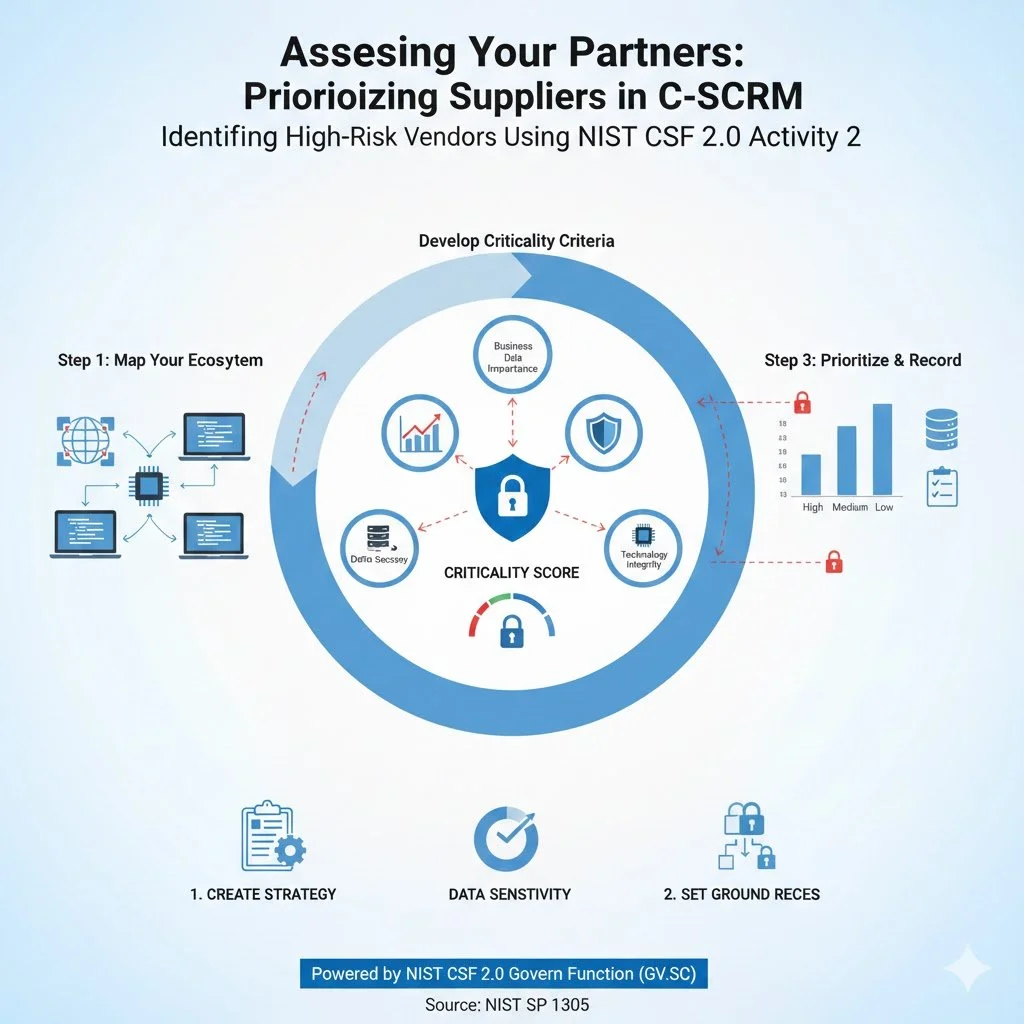
Step 1: Map Your Ecosystem
Before you can rank your suppliers, you must know who they are. The supply chain ecosystem is vast and includes:
Acquirers and Suppliers: The direct entities you buy from.
Developers and System Integrators: The teams building your software or connecting your hardware.
External Service Providers: Cloud hosts, data centers, and digital service partners.
Step 2: Develop Your Criticality Criteria
NIST recommends creating a standardized set of criteria to determine how "critical" a supplier is to your mission8. Consider these four factors:
Business Importance: How vital is the supplier's product or service to your daily operations?
Data Sensitivity: Does the supplier process or store sensitive or regulated data?.
System Access: What degree of access does the supplier have to your internal systems and networks?.
Technology Integrity: Is the hardware or software they provide a core component of your final product?.
Step 3: Prioritize and Record
Once your criteria are set, you should categorize suppliers into "Criticality Levels" (e.g., High, Medium, Low).
High-Criticality: These suppliers require the most robust security requirements and frequent monitoring.
Low-Criticality: These may only require standard contractual language.
It is essential to keep a record of all suppliers, prioritized by these criteria, to serve as a single source of truth for your security and procurement teams.
Why This Matters for 2026 Compliance
Under the NIST CSF 2.0 Govern Function (GV.SC), managing these risks is no longer optional. By prioritizing your suppliers now, you ensure that your most limited resources—time and budget—are spent protecting the most vulnerable parts of your business.
👉 Request your customized cyber vulnerability report today and stay ahead of threats.
👉 Gain insights into your unique cybersecurity vulnerabilities with a custom report.
👉 Train your team to be your first line of defense
📞 Schedule a call today or 📧 contact us for a consultation.