AI Is Changing Cybersecurity — Here’s What NIST Wants Organizations to Do About It
Why AI Changes the Compliance Conversation
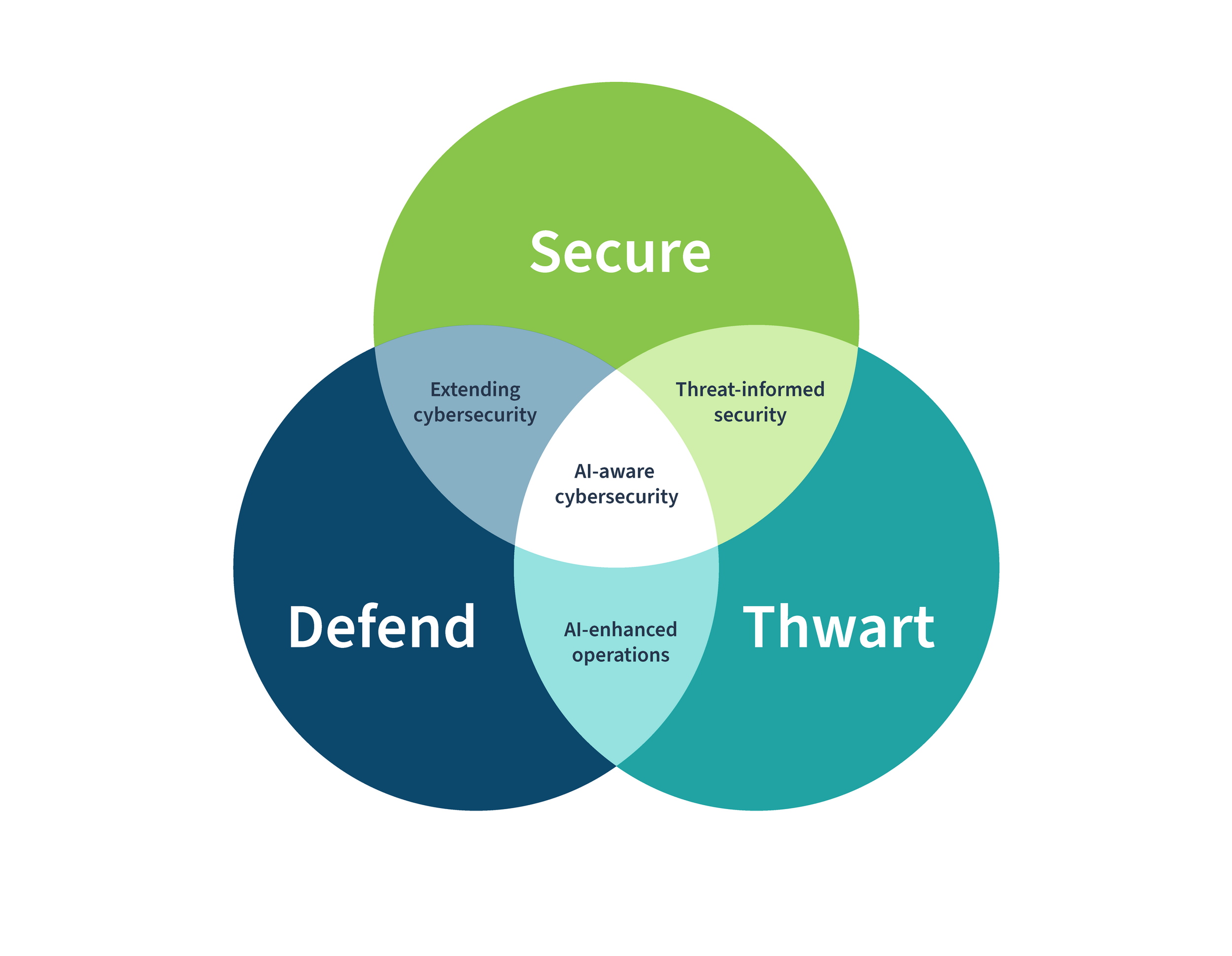
Artificial Intelligence is no longer a “future technology.”
It’s already writing emails, analyzing data, approving transactions, and helping teams make decisions.
But here’s the problem most organizations haven’t addressed yet:
If AI becomes part of your business, it also becomes part of your cybersecurity risk—and your compliance responsibility.
That’s why NIST has released new draft guidance focused specifically on AI and cybersecurity, helping organizations understand how to use AI safely without breaking trust, rules, or regulations.