1. What Is SharePoint — and Who’s Affected?
SharePoint is a document‑sharing platform that many organizations run on their own servers, not the cloud. These are called on‑premises SharePoint servers, and they’re widely used in schools, hospitals, government agencies, and businesses
2. What’s Broken — The “ToolShell” Exploit
In mid‑July 2025, researchers discovered a critical vulnerability (CVE‑2025‑53770) affecting on‑prem SharePoint servers. This flaw allows hackers to break into SharePoint without login credentials by sending manipulated web requests (“spoofing”)
The exploit (nicknamed “ToolShell”) chains that flaw with another (CVE‑2025‑53771). Together, they let attackers upload a hidden script (a web shell) that gives full control over the server—including reading encrypted keys and deploying malware like ransomware
3. Who’s Behind the Attacks?
Microsoft has identified at least three China-related hacking groups—Linen Typhoon, Violet Typhoon, and Storm‑2603—actively exploiting this vulnerability. Some groups have already deployed Warlock ransomware on compromised systems
4. What Damage Has Been Done?
Roughly 100 organizations worldwide have been confirmed compromised, including U.S. federal agencies, government departments in Germany, energy and finance companies in the U.S. and Europe
Check Point and Microsoft telemetry show tens of thousands of other servers remain unpatched and vulnerable—some estimates even suggest up to 8,000–4,600 attempts targeting hundreds of organizations globall
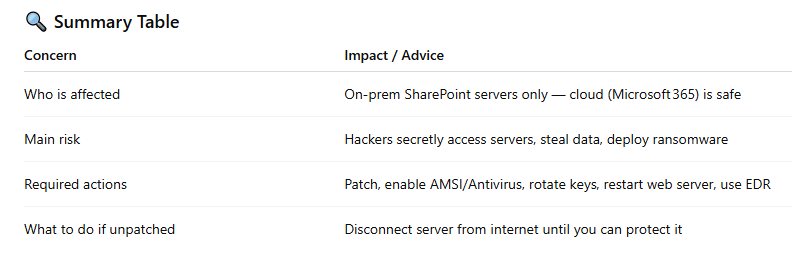
5. Am I Safe If I Use SharePoint Online (Cloud)?
Yes. SharePoint Online (Microsoft 365 cloud) is not affected by this attack. Only on‑premises SharePoint servers must take action.
6. What You Should Do Right Now
If your organization runs on‑prem SharePoint (Server 2016, 2019, or Subscription Edition):
Apply Microsoft’s emergency security updates issued July 20–22, 2025, covering CVE‑2025‑53770 and CVE‑2025‑53771 or older related flaws
Enable Antimalware Scan Interface (AMSI) in Full Mode, and run Microsoft Defender Antivirus or an equivalent tool on all servers to catch any malicious behavior
Rotate ASP.NET Machine Keys and restart IIS (the web server software) to remove backdoors installed by attackers .
Enable Endpoint Detection tools (EDR) to monitor and detect malicious activity post-breach
If your SharePoint server is public-facing and you can't patch immediately, disconnect it from the internet until protections are configured
7. Why This Is Serious
The exploit lets attackers act anonymously, without needing any user account or interaction.
It can steal cryptographic keys, deploy malware, and shut down or spy on systems quietly.
Because it affects older, on‑prem systems—and defaults to internet visibility in some setups—attackers can hit many unpatched targets automatically
🧠 Bottom Line
This is one of the most urgent security incidents Microsoft has released this year. If you're managing your own SharePoint server, act immediately. It's not just about patching—it’s about stopping attackers who may already be inside.
References:
UPDATE: Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities | CISA
https://www.microsoft.com/en-us/security/blog/2025/07/22/disrupting-active-exploitation-of-on-premises-sharepoint-vulnerabilities/
👉 Book a free compliance readiness assessment
👉 Get a customized cybersecurity roadmap
👉 Train your team to be your first line of defense
📞 Schedule a call today or 📧 contact us for a consultation.